A rootkit is a program or, more often, a collection of software tools that gives a threat actor remote access to and control over a computer or other system. Rootkits can run in either User mode or Kernel mode, with Kernel mode being the most dangerous. There are legitimate rootkits out there, for example Anti-Virus software or Remote Access software. Rootkits can be difficult to detect as they control the way that the operating system behaves or interacts with the user.
1. Memory Dump with Analysis Using Redline
This method is the most effective as it is impossible for malware to hide in memory, by performing a memory dump and analyzing the memory, this option is the most thorough however it is also the most complex.
Take a memory dump of your system, for a quick easy utilize dumpit, start Redline and select analyze memory file
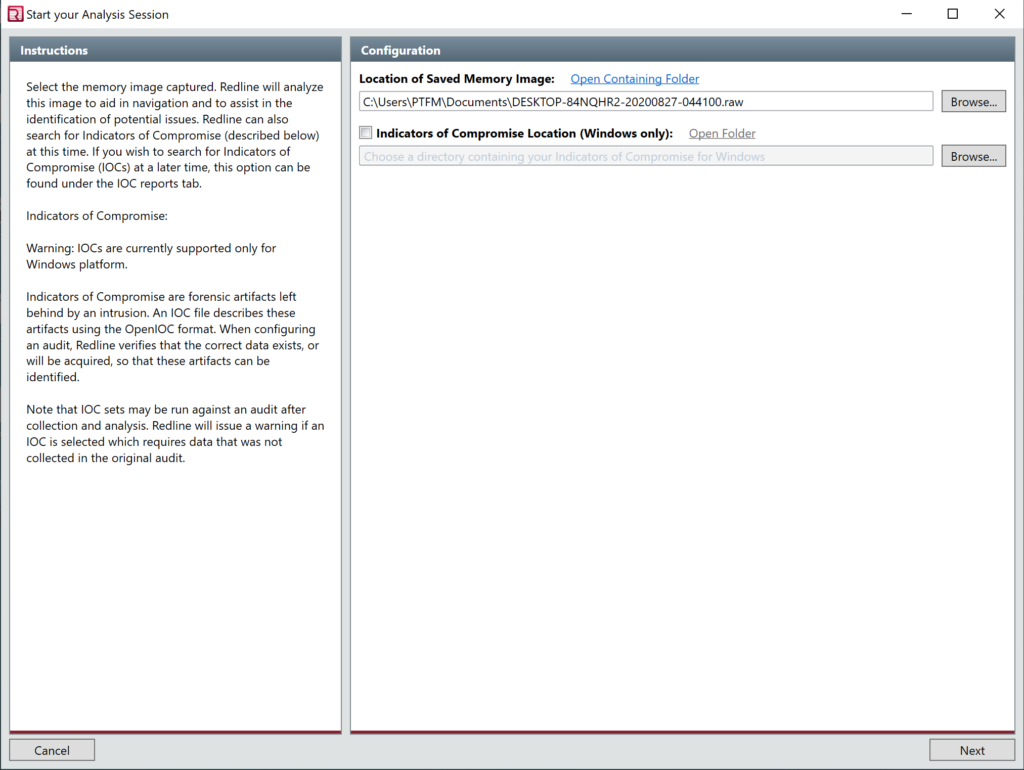
Click next and select output filename and directory
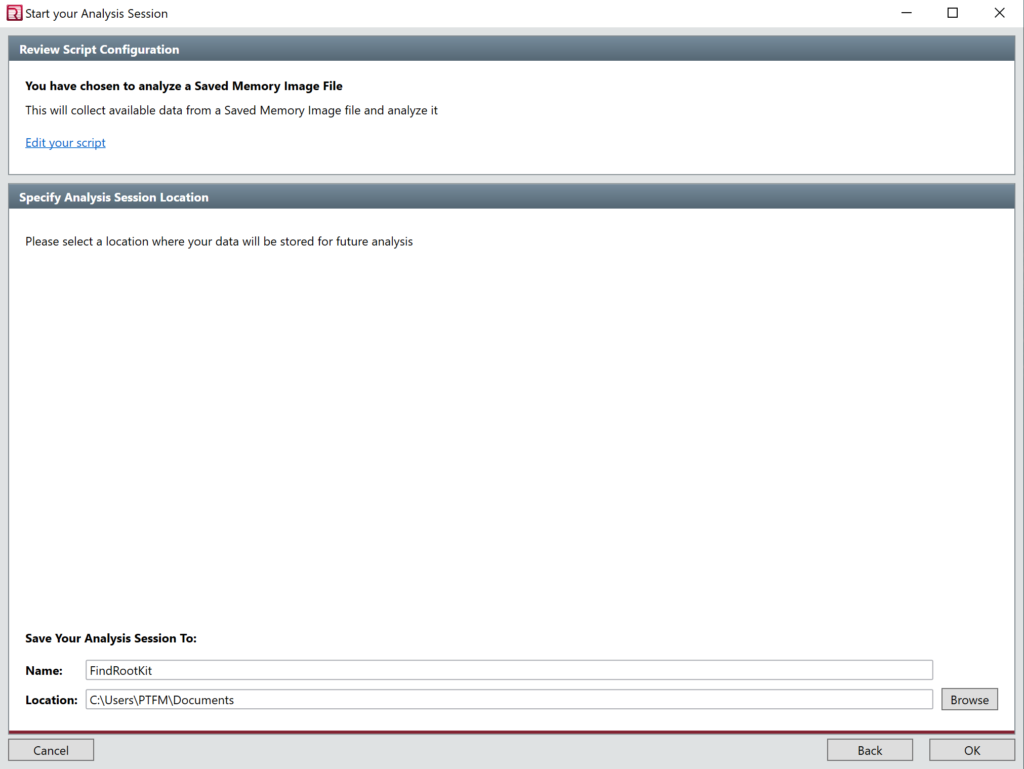
Click Ok the next screen may take some time
2. Windows Defender Offline Scans
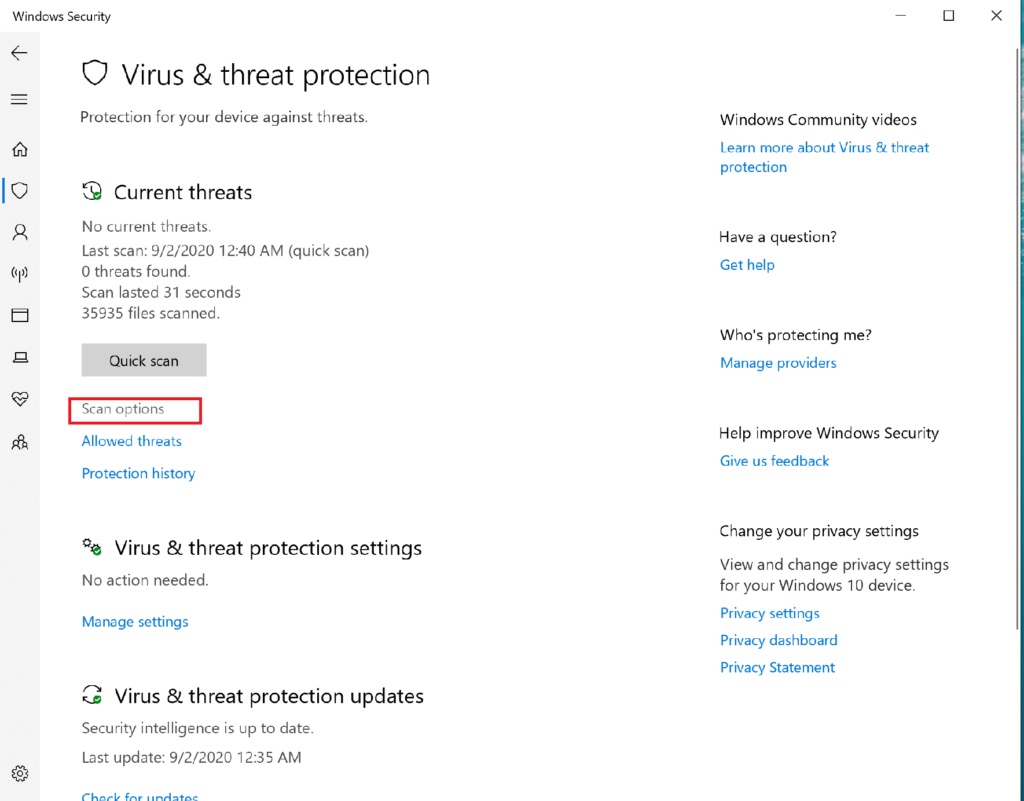
Open Windows Security and Select Virus and Threat Protection then Select Scan Options
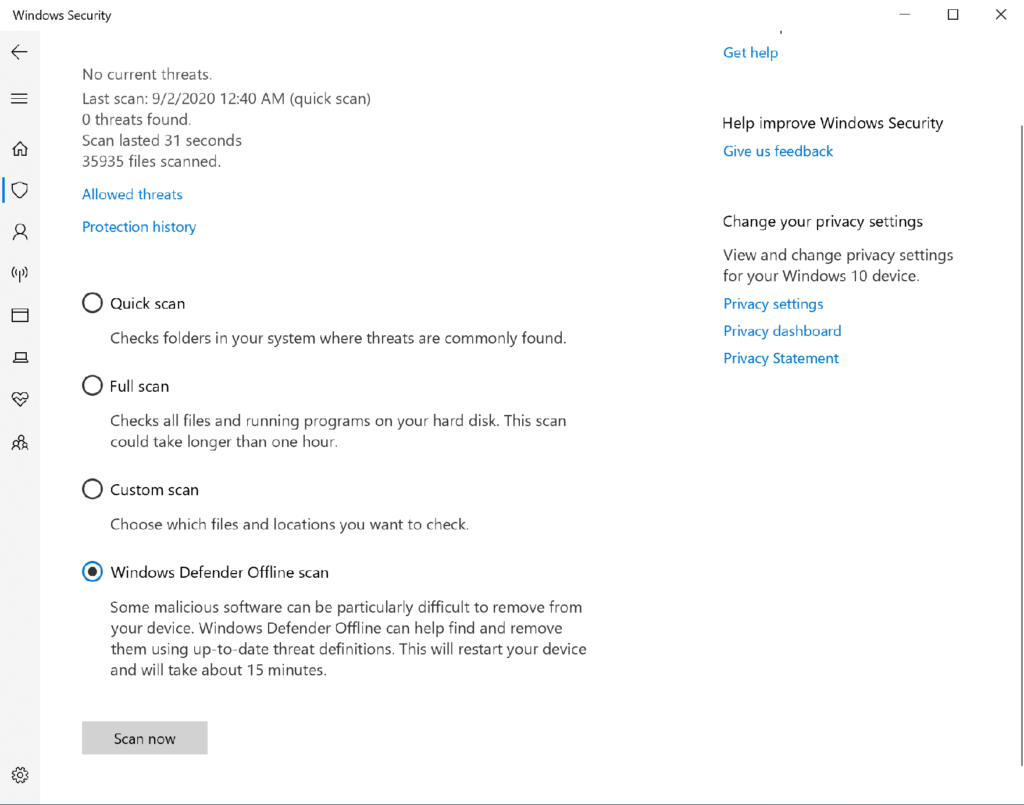
Select Windows Defender Offline scan and select scan now, this will trigger a restart and will scan the filesystem in a “Safe Mode”
3. GMER
You can download GMER here (Caution will download EXE) or go to GMER site to download here
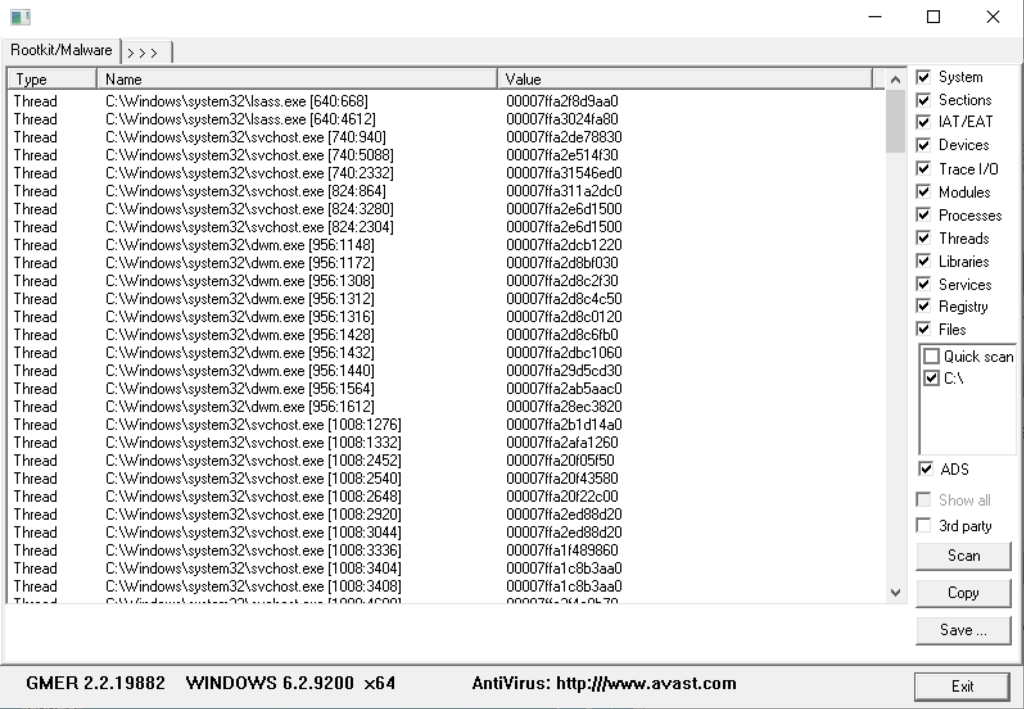
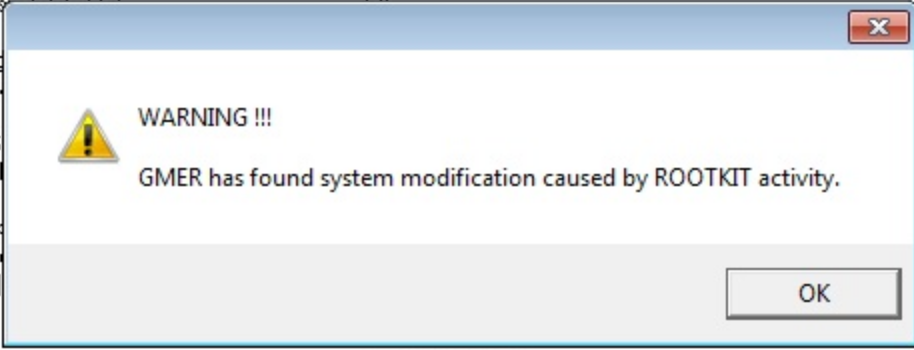
Once downloaded run and select Scan. GMER will then attempt to find any rootkits by scanning files, registry entries, drives and processes. After scan is finished you will see one of the following windows indicating the results.